ICISS 2025 - The 21st Annual International Information System Security Conference
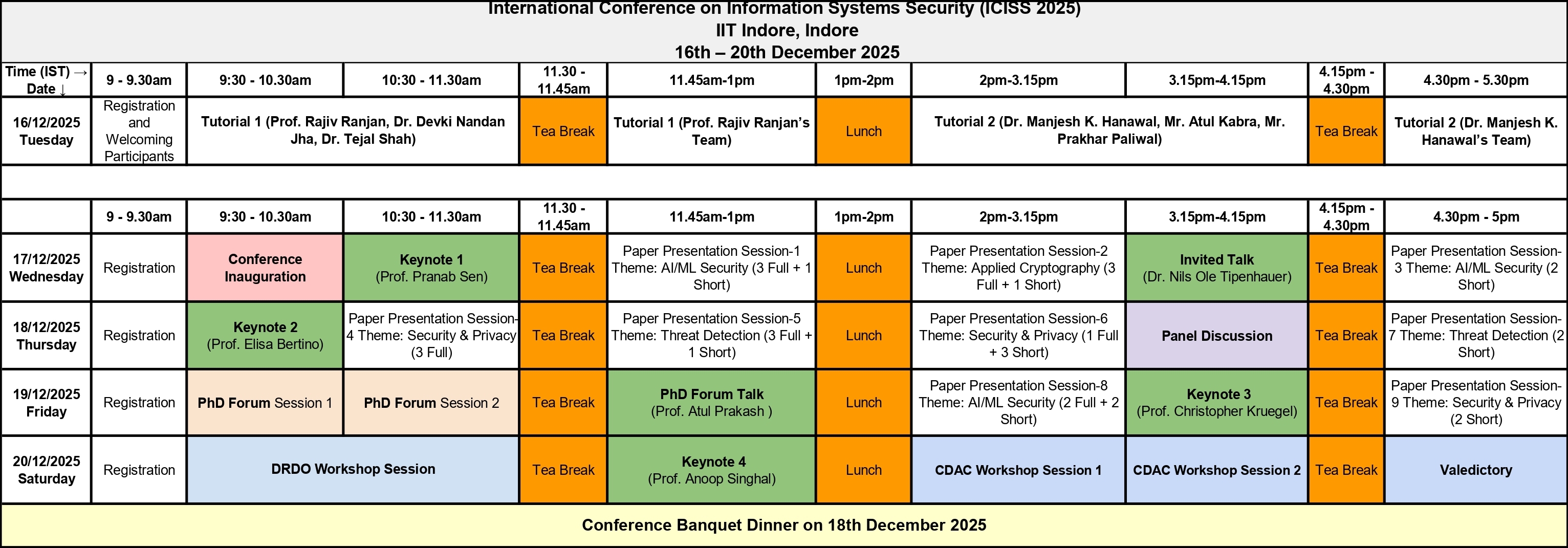
Program At-A-Glance
Detailed Program
DAY 1 PROGRAM – TUESDAY, DECEMBER 16
| Time (IST) | Event | |
| 09:00 – 09:30 | Registration and Welcoming Participants | |
| 09:30 – 11:30 | TUTORIAL 1: Federated Learning: Architecture, Threat
Landscape, and Defence
Mechanisms Speakers: Prof. Rajiv Ranjan (Newcastle University, UK), Dr. Devki Nandan Jha (Newcastle University, UK), Dr. Tejal Shah (Newcastle University, UK) |
|
| 11:30 – 11:45 | TEA BREAK | |
| 11:45 – 13:00 | TUTORIAL 1 (Prof. Rajiv Ranjan’s Team) | |
| 13:00 – 14:00 | LUNCH | |
| 14:00 – 16:15 | TUTORIAL 2: Vajra-Sandbox: A Robust Framework for
Malware Execution and
Analysis Speakers:Dr. Manjesh Kumar Hanawal (IIT Bombay), Mr. Atul Kabra (ReliaQuest, Bengaluru), Mr. Prakhar Paliwal (IIT Bombay) |
|
| 16:15 – 16:30 | TEA BREAK | |
| 16:30 – 17:30 | TUTORIAL 2 (Dr. Manjesh Kumar Hanawal’s Team) | |
DAY 2 PROGRAM – WEDNESDAY, DECEMBER 17
| Time (IST) | Event | ||||||||
| 09:00 – 09:30 | Registration | ||||||||
| 09:30 – 10:30 | Conference Inauguration | ||||||||
| 10:30 – 11:30 | KEYNOTE 1: Practical Resilient Efficient
Quantum Key Distribution Speaker: Prof. Pranab Sen (TIFR, Mumbai) |
||||||||
| 11:30 – 11:45 | TEA BREAK | ||||||||
| 11:45 – 13:00 |
|
||||||||
| 13:00 – 14:00 | LUNCH | ||||||||
| 14:00 – 15:15 |
Paper Presentation Session 2: Applied Cryptography
|
||||||||
| 15:15 – 16:15 | INVITED TALK: Reverse Engineering Industrial Control
Devices Speaker: Dr. Nils Ole Tippenhauer (CISPA, Germany) |
||||||||
| 16:15 – 16:30 | TEA BREAK | ||||||||
| 16:30 – 17:00 |
Paper Presentation Session 3: AI/ML Security
|
||||||||
DAY 3 PROGRAM – THURSDAY, DECEMBER 18
| Time (IST) | Event | ||||||||||
| 09:00 – 09:30 | Registration | ||||||||||
| 09:30 – 10:30 | KEYNOTE 2: AI Agentic Security: Safeguarding
the Next Generation of Autonomous
Systems Speaker: Prof. Elisa Bertino (Purdue University) |
||||||||||
| 10:30 – 11:30 |
Paper Presentation Session 4: Security & Privacy
|
||||||||||
| 11:30 – 11:45 | TEA BREAK | ||||||||||
| 11:45 – 13:00 |
Paper Presentation Session 5: Threat Detection
|
||||||||||
| 13:00 – 14:00 | LUNCH | ||||||||||
| 14:00 – 15:15 |
Paper Presentation Session 6: Security & Privacy
|
||||||||||
| 15:15 – 16:15 | PANEL DISCUSSION | ||||||||||
| 16:15 – 16:30 | TEA BREAK | ||||||||||
| 16:30 – 17:00 |
Paper Presentation Session 7: Threat Detection
|
||||||||||
| CONFERENCE BANQUET DINNER |
DAY 4 PROGRAM – FRIDAY, DECEMBER 19
| Time (IST) | Event | ||||||||||
| 09:00 – 09:30 | Registration | ||||||||||
| 09:30 – 10:30 | PhD Forum Session 1 | ||||||||||
| 10:30 – 11:30 | PhD Forum Session 2 | ||||||||||
| 11:30 – 11:45 | TEA BREAK | ||||||||||
| 11:45 – 13:00 | PHD FORUM TALK: Towards Developing Skills for
Writing Great Papers and Giving Great
Talks Speaker: Prof. Atul Prakash (University of Michigan, Ann Arbor) |
||||||||||
| 13:00 – 14:00 | LUNCH | ||||||||||
| 14:00 – 15:15 |
Paper Presentation Session 8: AI/ML Security
|
||||||||||
| 15:15 – 16:15 | KEYNOTE 3: Smart Contracts, Dumb Mistakes:
Understanding and Preventing DeFi
Exploits Speaker: Prof. Christopher Kruegel (University of California, Santa Barbara) |
||||||||||
| 16:15 – 16:30 | TEA BREAK | ||||||||||
| 16:30 – 17:00 |
Paper Presentation Session 9: Security & Privacy
|
||||||||||
DAY 5 PROGRAM – SATURDAY, DECEMBER 20
| Time (IST) | Event | |
| 09:00 – 09:30 | Registration | |
| 09:30 – 11:30 | DRDO Workshop Session Title: NIGHUD (Network Information Gathering of Hidden Unseen Data) |
|
| 11:30 – 11:45 | TEA BREAK | |
| 11:45 – 13:00 | KEYNOTE 4: Threat Modeling for Security of
Machine Learning
Systems Speaker: Dr. Anoop Singhal (NIST, Gaithersburg) |
|
| 13:00 – 14:00 | LUNCH | |
| 14:00 – 16:15 | CDAC Workshop Session Title: Digital Trust for IoT Ecosystems: From Secure Identities to Quantum-Resilient Security |
|
| 16:15 – 16:30 | TEA BREAK | |
| 16:30 – 17:00 | Valedictory Session | |